PSA: Hackers can steal your username and password for an internet site utilizing an embedded iframe. It is a weak spot for all password managers, and most have addressed the flaw in numerous methods, together with issuing warnings when customers are on a login web page with an iframe or not trusting subdomains. Bitwarden is the only exception, having decided in 2018 that the risk was not vital sufficient to handle.
In its help pages relating to “Auto-fill,” Bitwarden advises customers to show off their browsers’ password autofill features as a result of they intervene with its password administration resolution. It additionally mentions it’s a good suggestion as a result of “specialists usually agree that in-built [browser] password managers are extra susceptible than devoted options like Bitwarden,” which is usually true.
Sadly, its password filler won’t be a lot better than your browser’s. Safety researchers at Flashpoint found that Bitwarden’s autofill extension handles web sites with embedded iframes in an unsafe method. A fundamental understanding of iframes is required to grasp this vulnerability.
Web site builders use the inline body component, or iframe, to embed a part of one other webpage into their web site. For instance, TechSpot makes use of iframes to embed YouTube movies into its articles. It will also be used to embed internet types. Typically, iframes are secure to make use of so long as the embedded materials from the exterior web site has not been compromised, and that is the place managers have an issue.
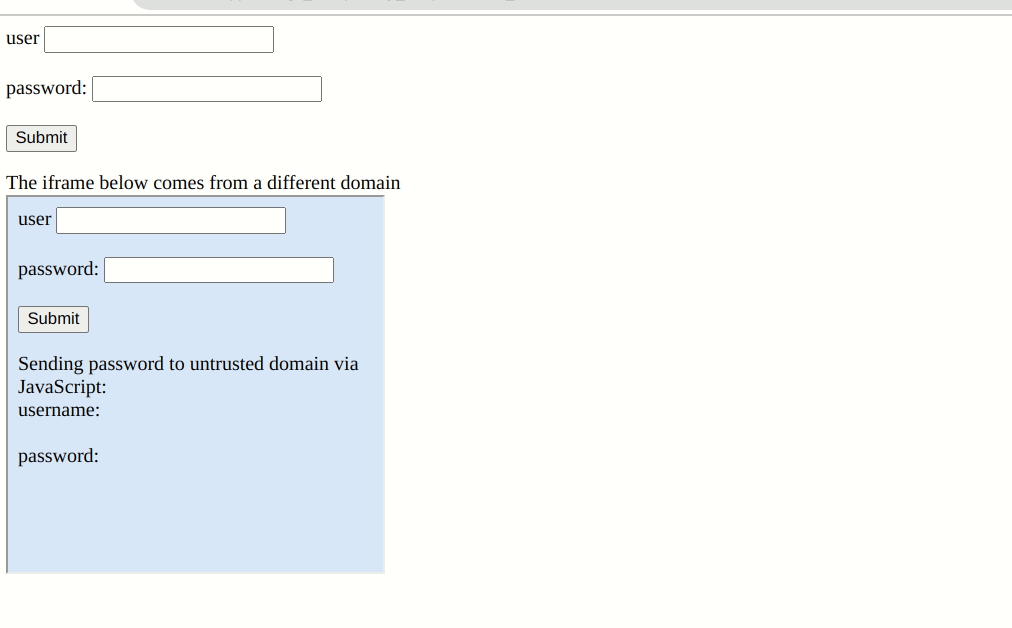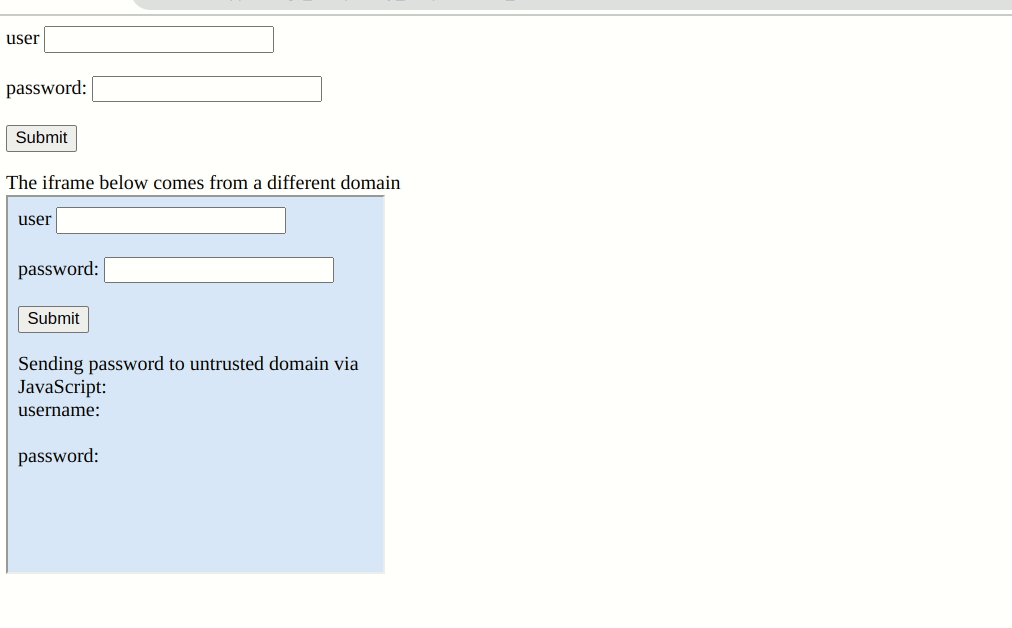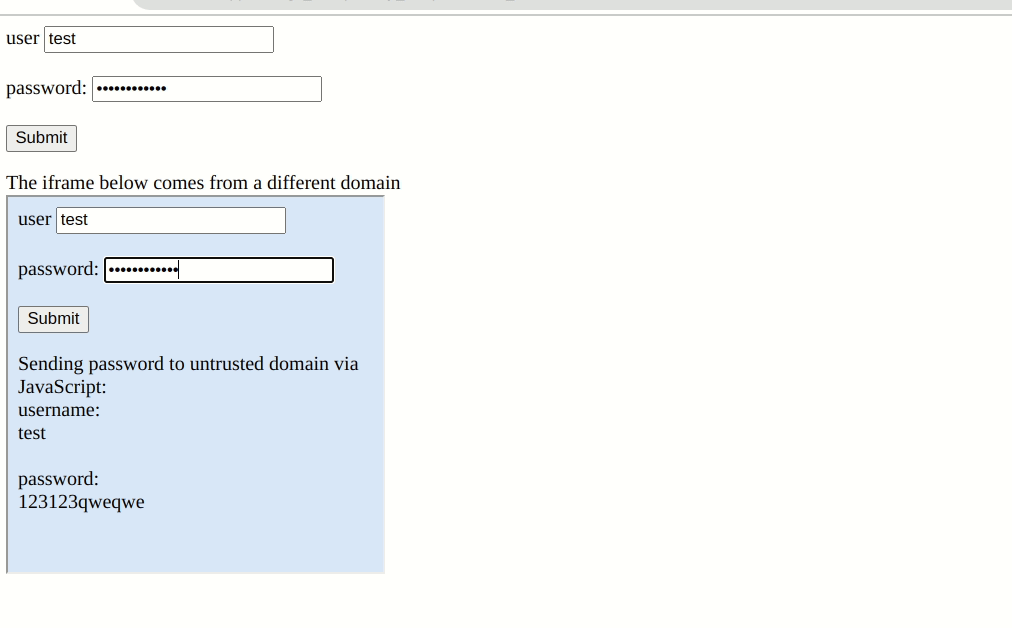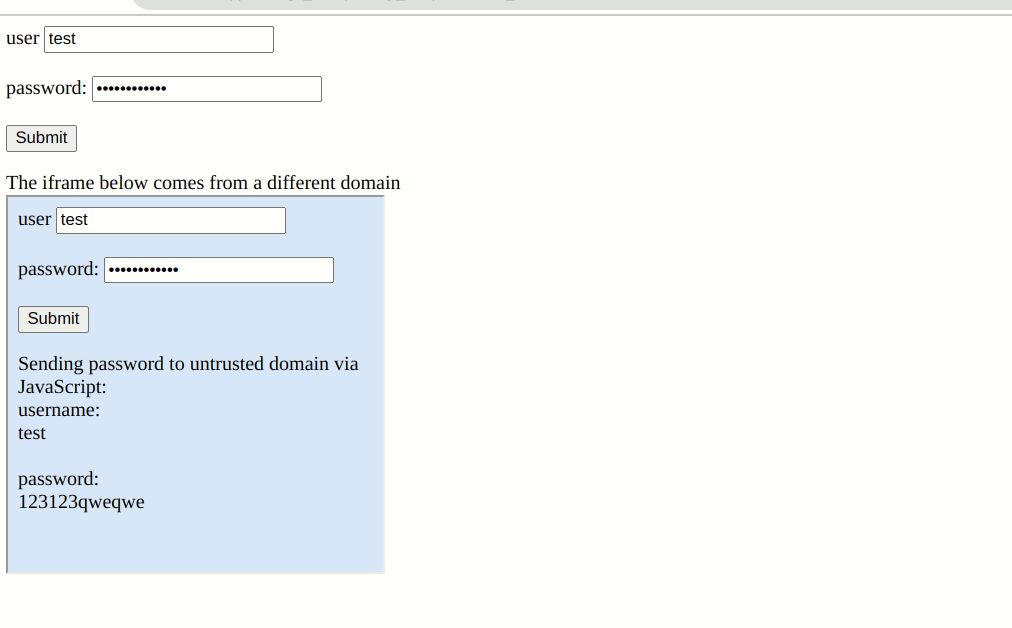
Password extensions autofill credentials on any webpage customers have saved their credentials by design. They will even fill out the login type pre-emptively with out consumer interplay. In Bitwarden’s thesis a setting referred to as “Auto-fill on web page load.” Nevertheless, the extension will carry out this operate in an iframe with out performing a “Similar-origin Coverage” test. So if a web page has a malicious iframe from a special area, the supervisor will unknowingly hand over your credentials for them to be despatched to a hacker’s server.
Most password managers have checks in place to at the very least warn customers of potential risks. Nevertheless, Bitwarden doesn’t forestall or warn that an iframe from a special area is doubtlessly stealing credentials. It assumes that every one iframes on a login web page are secure. It stated as a lot in a 2018 safety report, however extra on that later.
In fact, this might solely occur if the trusted web site is already compromised, proper? In keeping with Flashpoint, that is not essentially true.
Clearly, if hackers have gained sufficient of a foothold to embed an iframe on a official web site, customers have greater issues than this weak spot on their palms. There’s little that any password administration extension might do in that situation. Nevertheless, some official web sites use types from one other area, embedding them with an iframe. If hackers can compromise the secondary supply, they’ve a proxy for stealing data from the trusted web site.
Flashpoint admits it is a uncommon situation and confirmed that with a spot-check of a number of websites utilizing iframes on their login pages. Nevertheless, there’s one other drawback. Bitwarden’s default URI (Uniform Useful resource Identifier) matching is about to “Base area.” So the extension will present password autofill so long as the top-level and second-level domains match.
The issue is that a number of internet hosting providers enable customers to host “arbitrary content material” beneath a subdomain making it comparatively simple to spoof a login web page.
“For example, ought to an organization have a login web page at https://logins.firm.tld and permit customers to serve content material beneath https://[clientname].firm.tld, these customers are in a position to steal credentials from the Bitwarden extensions,” stated Flashpoint. “In our analysis, we confirmed that a few main web sites present this actual setting. If a consumer with a Bitwarden browser extension visits a specifically crafted web page hosted in these internet providers, an attacker is ready to steal the credentials saved for the respective area.”
Oddly, when Flashpoint contacted Bitwarden about this weak spot to coordinate disclosure, the corporate identified that it has identified about it since 2018.
“Since Bitwarden doesn’t test every iframe’s URL, it’s doable for an internet site to have a malicious iframe embedded, which Bitwarden will autofill with the ‘top-level’ web site credentials,” the corporate’s 2018 Safety Evaluation Report reads. “Sadly, there are official circumstances the place web sites will embrace iframe login types from a separate area than their ‘guardian’ web site’s area. No motion is deliberate presently.”
In different phrases, Bitwarden is conscious of the issue however deems the chance acceptable sufficient to not do something about it, even when it have been so simple as having the extension subject a warning when there’s an iframe on a web page. Flashpoint discovered this inexplicable since all of Bitwarden’s opponents have some type of mitigation for this exploit.
The researchers created a proof of idea utilizing the flaw as an assault vector and a “working exploit” they carried out privately on a “distinguished internet hosting setting.” They hope that builders at Bitwarden will change their minds concerning the subject since no person had created such exploits in 2018 when the corporate initially assessed the weak spot. Till Bitwarden addresses the vulnerability, you are able to do a few issues to mitigate it with out switching password managers.
First, flip off the extension’s “Auto-fill on web page load” setting. You’ll have to set off the autofill characteristic manually on a regular basis. Nevertheless, it provides you some respiratory room to examine the login web page with out instantly handing your credentials over to an iframe. That’s truly good recommendation for any password supervisor extension that includes preemptive autofill.
Second, use that pause to make certain you might be on a trusted area and that the web page is what it appears. Have a look at the URL to make sure you are on the proper area or subdomain and that nothing seems suspicious. For example, one thing like “login.wellsfargo.com” might be legit, whereas “credx257.wellsfargo.com” possible is not.
These steps will nonetheless not shield you from websites that use compromised exterior internet types, however Flashpoint famous that these eventualities are uncommon. It is no cause to surrender utilizing a password supervisor, even Bitwarden. Managers are well-suited that can assist you preserve your credentials straight. It is all the time higher to have tons of stable hard-to-remember passwords distinctive to each web site than to reuse weak ones.