What simply occurred? The Emotet botnet was lifeless, or so researchers thought. The malicious community is now again in enterprise with a brand new phishing marketing campaign, exploiting a novel approach to push customers and corporations to contaminate themselves.
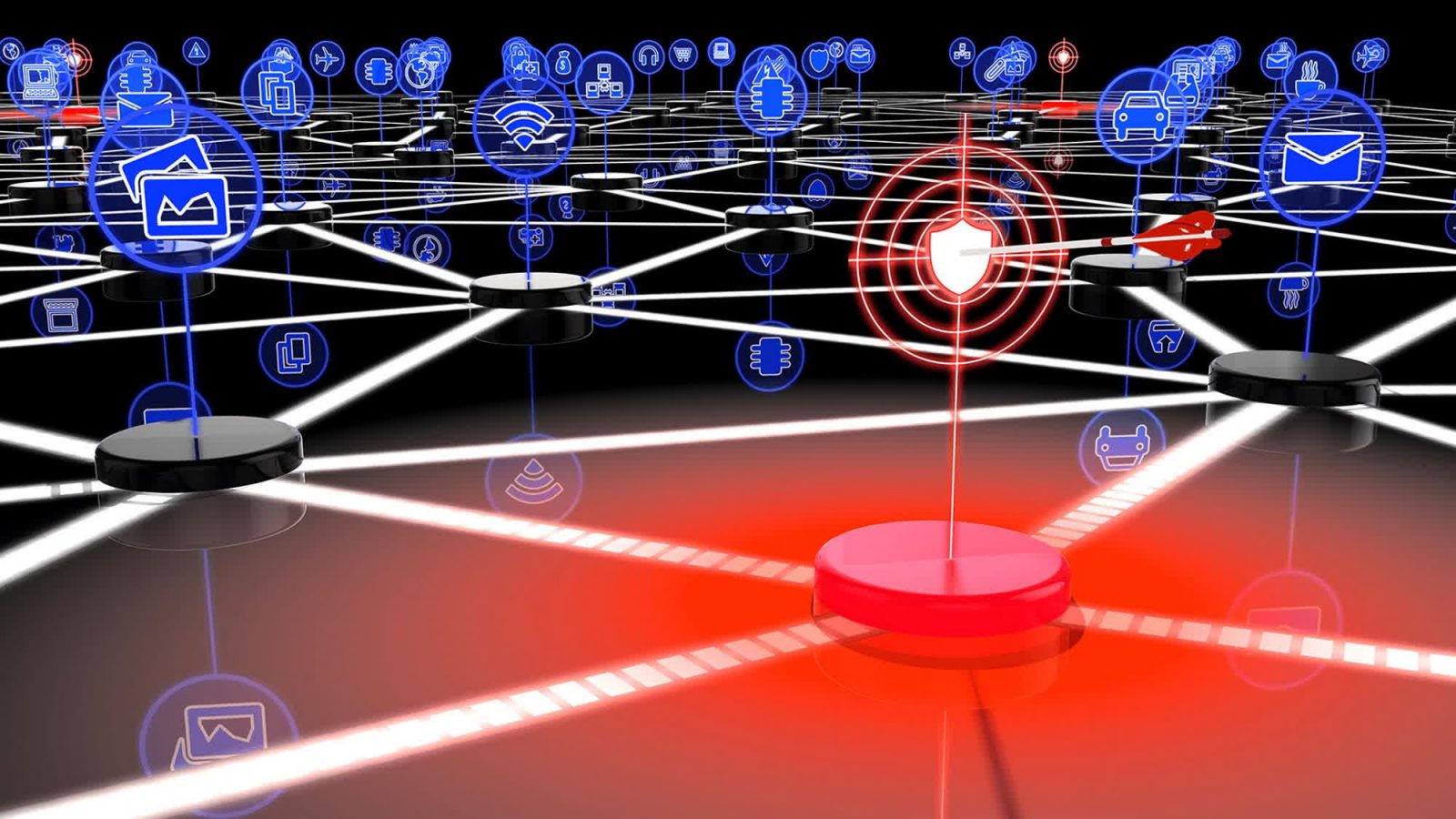
After a 4-month hiatus, Emotet is once more energetic as one of the vital harmful botnet operations on the market. Cyber-criminals are utilizing the community to unfold malicious software program and different potential infections, with a brand new trick designed to bypass protections in Microsoft Workplace purposes.
Emotet was thought-about one of the vital widespread infections till July 2022, when the community instantly stopped spamming campaigns and third-party malware distribution. Now, the botnet is back in “distribution mode,” in accordance with the analysis group Cryptolaemus.
🚨Emotet again in Distro Mode🚨 – As of 0800 UTC E4 started spamming and as of 0930 UTC E5 started spamming once more. Appears like Ivan is in want of some money once more so he went again to work. Be looking out for direct connected XLS recordsdata and zipped and password protected XLS. 1/x
— Cryptolaemus (@Cryptolaemus1) November 2, 2022
The notorious Emotet botnet started spamming once more on November 2nd, with a brand new electronic mail phishing marketing campaign concentrating on stolen electronic mail reply chains. The community is now distributing malicious Excel attachments, sending them to customers talking completely different languages whereas pretending to be invoices, scans, varieties, and different partaking “baits.” The malware will also be Zip archives or password-protected XLS spreadsheets.
Emotet’s newest marketing campaign brings a brand new software to the botnet’s arsenal –an Excel template that features directions on bypassing Microsoft’s Protected View know-how. Protected View marks recordsdata from the web with a “Mark-of-the-Net” flag, which instructs Workplace purposes to open stated recordsdata in protected mode, thus avoiding direct execution of the connected macros.
The directions within the malicious spreadsheet advise customers to repeat the file into one of many “trusted” Template folders of Microsoft Workplace. When opened from trusted areas, the malicious doc will bypass Protected View executing the included macros and spreading the Emotet an infection.

The brand new Emotet malware downloads in Dll kind and executes on the system utilizing the respectable Regsvr32.exe software. As soon as energetic, Emotet sits quietly, ready for directions from the botnet’s command & management server. For now, the community would not appear to drop further malicious payloads because it did earlier than its vanishing act.
One of the vital infamous options of Emotet has at all times been the flexibility to work in partnership with different malicious operations, spreading harmful malware like TrickBot, Cobalt Strike, and others. Prior to now, Emotet was a robust power behind ransomware attackers like Ryuk, Conti, BlackCat, and Quantum. The botnet supplied preliminary entry to already contaminated networks and units for simpler ransomware spreading.