What simply occurred? Months after researchers found the harmful, “invisible” menace posed by BlackLotus, Microsoft is now giving investigators and sysadmins an in depth steering over the telltale indicators of an ongoing an infection.
BlackLotus is an omnipotent UEFI bootkit just lately found “within the wild,” a safety menace geared up with very superior capabilities and designed to show itself into an invisible ghost inside a completely up to date Home windows machine. Regardless that the an infection is successfully clear to regular utilization, researchers and analysts have now sufficient data in regards to the system modifications introduced by the malware.
Microsoft has put collectively a steering for investigating (and, after all, detecting) the BlackLotus marketing campaign, which is first designed to use the CVE-2022-21894 safety flaw (“Safe Boot Safety Characteristic Bypass Vulnerability”) mounted by Redmond in January 2022. UEFI bootkits are significantly harmful as they run at laptop startup earlier than the working system is loaded, Microsoft explains, subsequently they’ll intervene with or deactivate varied OS safety mechanisms.
In line with Microsoft’s information, researchers and directors should search particular (hidden) elements of a Home windows set up to establish the clues of a BlackLotus an infection. The telltale indicators of the bootkit presence embody just lately created and locked boot information, a staging listing used in the course of the BlackLotus set up, Registry key modifications to disable the Hypervisor-protected Code Integrity (HVCI) function, and community and boot logs.
To analyze the potential modifications to the boot course of, Microsoft says, “menace hunters” first have to mount the EFI system partition that’s normally hidden from on a regular basis Home windows use. Then they must test the modification date of the EFI information protected by the BlackLotus kernel driver, looking for mismatches between earlier and the latest information. The current ones would seemingly be related to the bootkit an infection.
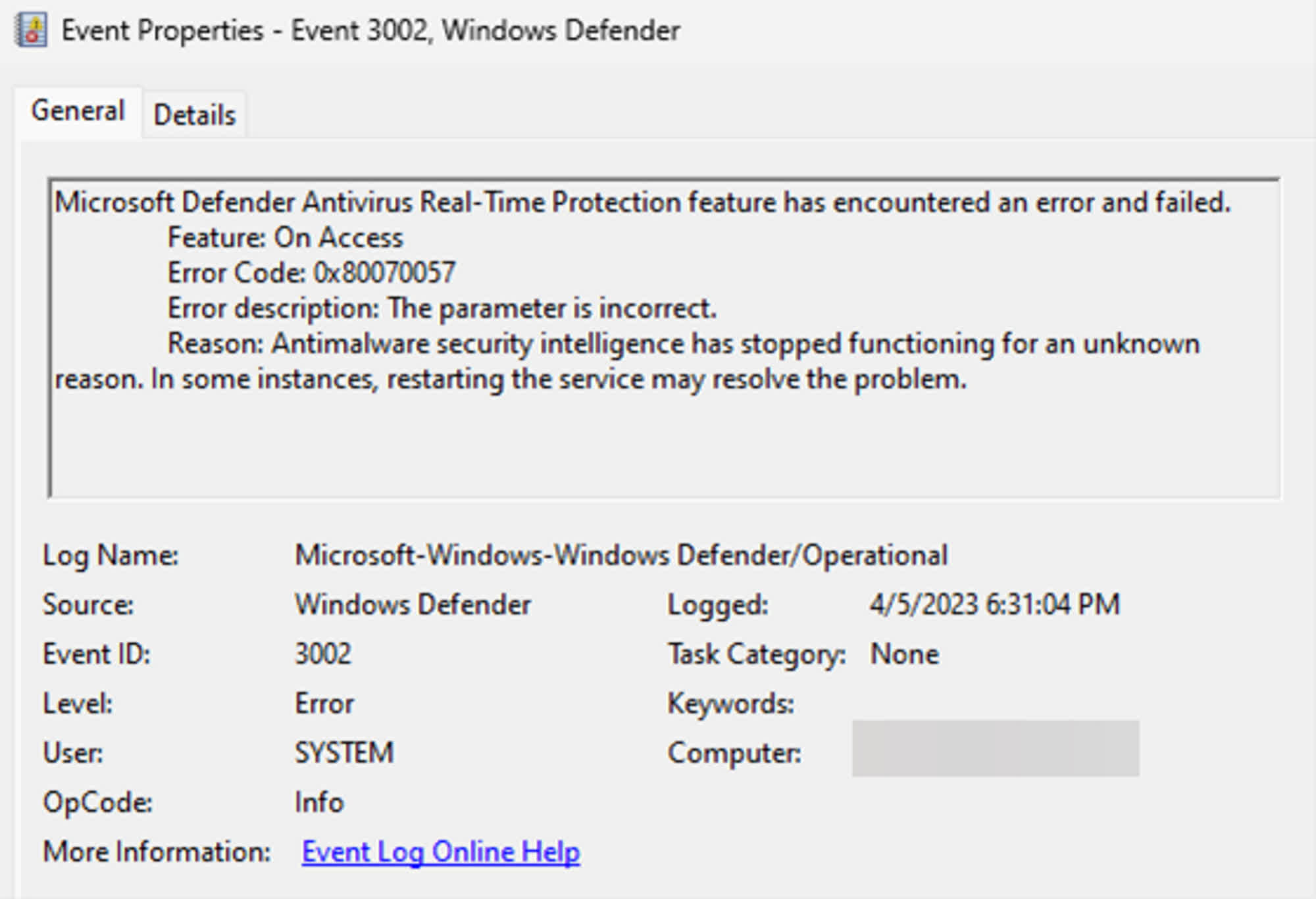
A BlackLotus an infection may also be detected by looking for a “system32” folder inside the EFI partition, which is the situation the place the malware set up is began. BlackLotus additionally modifies the Home windows Registry to disable HVCI, whereas the Defender antivirus would not begin anymore. Investigators can seek for traces within the Home windows Occasion Logs, together with an “ID 7023” occasion generated when the Defender real-time safety service will get stopped “for an unknown cause.”
Logs of outbound connections from winlogon.exe on port 80 may also reveal BlackLotus presence on the machine, because the bootkit’s injected HTTP loader tries to succeed in the command&management server or carry out “community configuration discovery.” When the bootkit turns into energetic, Microsoft explains, two new boot drivers (“grubx64.efi,” “winload.efi”) may be seen by evaluating logs.
Microsoft additionally supplies directions on learn how to forestall and take away a BlackLotus an infection. Prevention is one of the best answer towards conventional and invisible threats, Microsoft suggests, and system directors ought to first keep away from using domain-wide, admin-level service accounts by proscribing native administrative privileges. Implementing a number of layers of safety controls is the one technique that may scale back dangers, whereas disinfection may be achieved however requires a cautious reinstallation of a clear working system, EFI partition and UEFI firmware.