Why it issues: Microsoft has issued steerage for fixing a severe Safe Boot vulnerability that impacts all Home windows methods and is actively being exploited within the wild. Usually, this type of problem can be patched by way of month-to-month servicing updates however the Redmond firm has chosen a phased strategy to scale back the chance of you or your group ending up with gadgets that will not boot. The repair would require some guide steps for now, however will likely be utilized routinely on all supported Home windows methods beginning subsequent 12 months.
Microsoft’s newest Patch Tuesday updates are out for Home windows 11 and Home windows 10 with a number of fixes for 2 working methods. Within the case of Home windows 11, the KB5026372 cumulative replace introduces a minimum of 20 modifications that enhance the consumer expertise in addition to fixes for 38 safety vulnerabilities and three zero-days affecting varied Microsoft merchandise.
On the identical time, the Redmond firm has launched an optionally available safety replace addressing a vulnerability in Safe Boot that has been exploited within the wild via the BlackLotus UEFI malware, affecting even up-to-date Home windows methods. This impacts all supported variations of Home windows 11 and Home windows 10 and is tracked underneath CVE-2023-24932.
Mockingly, the principle goal of Safe Boot is to guard your PC from loading any untrusted code between the time you energy it on and the purpose the place Home windows takes management. In different phrases, it’s supposed to forestall hackers who acquire bodily entry to your machine from injecting booby-tapped code often known as a “bootkit” that modifies the startup course of.
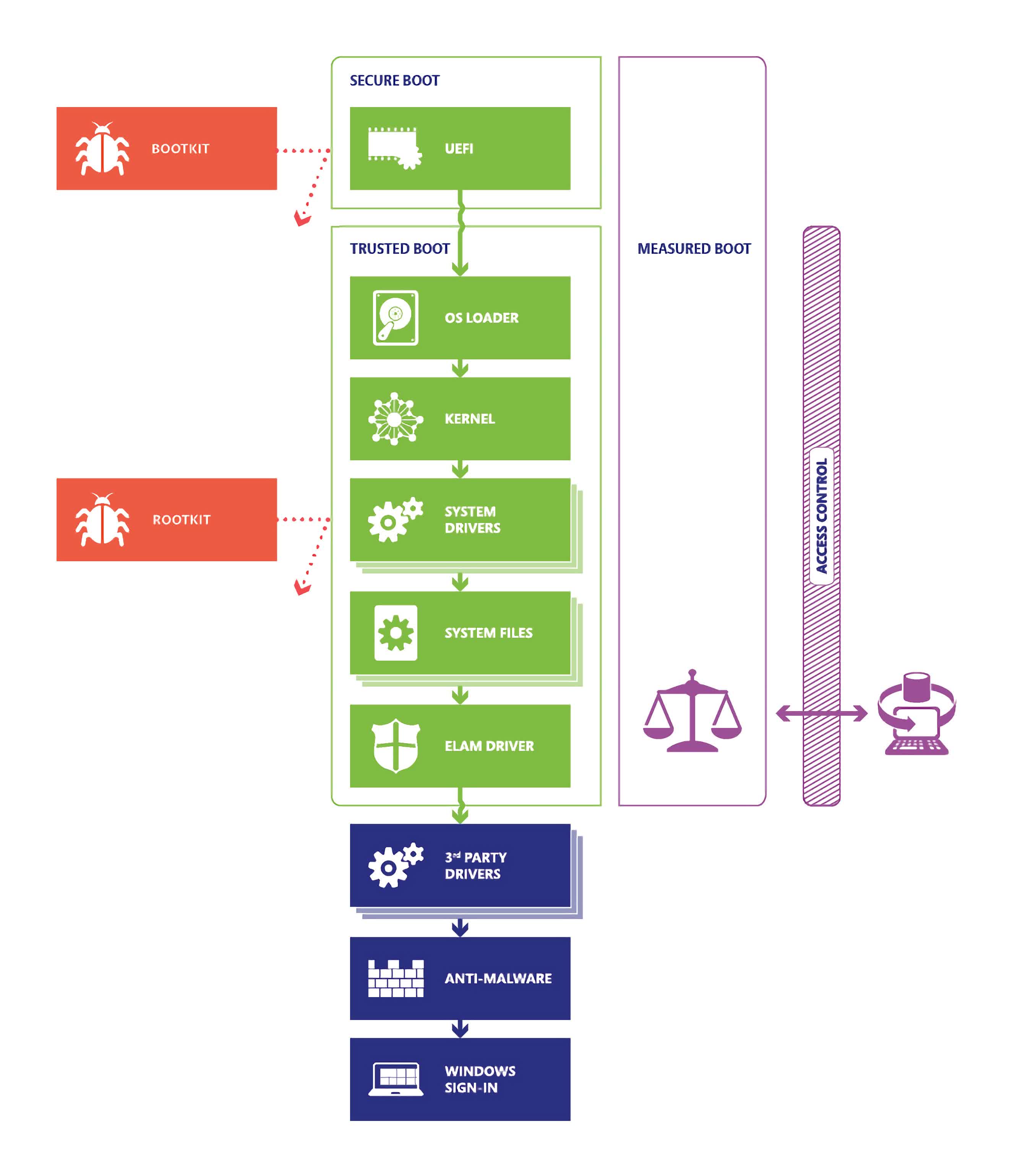
This exploit is called an “evil cleaner” assault, and permits a malicious actor to introduce malware that may log something you kind and extract it later with little or no effort. It may be so simple as booting your machine with a USB drive and letting an automatic script do all of the work.
Microsoft explains that every one Home windows methods with Safe Boot enabled are affected by the brand new flaw, together with on-premises gadgets, digital machines, and even cloud-based gadgets. It additionally impacts gadgets working any main Linux distributions, and we’re informed a repair is within the works. That mentioned, Microsoft is taking a phased strategy to deal with this vulnerability to reduce disruption and simplify deployment for big organizations.
This implies the repair is already current within the newest Patch Tuesday replace, however for now it requires some guide steps to allow it:
1. Set up the month-to-month servicing replace launched on Could 9 or afterward your entire Home windows gadgets and reboot them earlier than transferring on to the subsequent step.
2. Replace any bootable media and full backups of Home windows it’s important to guarantee all of them have the repair for CVE-2023-24932.
3. Apply the Home windows Boot Supervisor revocations to completely defend your methods from assaults that exploit the brand new vulnerability.
As a part of the second part, Microsoft will launch new steerage on July 11, 2023 with simplified replace choices that obtain the identical degree of safety in opposition to this assault. The ultimate part will begin someday within the first quarter of 2024, and it’ll see the repair for CVE-2023-24932 in addition to the Home windows Boot Supervisor revocations utilized to all supported Home windows methods routinely.
It is value noting that when you deploy all of the mitigations for the brand new flaw on a system, you will not be capable to revert these modifications. Additionally, to seek out out if Safe Boot is enabled in your machine, merely open the command immediate and run the “msinfo32,” which opens System Info. It’s best to be capable to discover an entry known as “Safe Boot State” within the System Abstract part.
Masthead credit score: FLY:D