In a nutshell: If you happen to’ve ever been redirected to a strange-looking Q&An internet site showing to advertise cryptocurrency or different blockchain applied sciences, it may very well be a part of an ad-click-pumping rip-off. Since final fall, 1000’s of contaminated web sites have been roped into these fraudulent schemes.
Safety researchers at Sucuri have spent the previous few months monitoring malware that diverts customers to fraudulent pages to inflate Google advert impressions. The marketing campaign has contaminated over 10,000 web sites, inflicting them to redirect guests to utterly completely different spam websites.
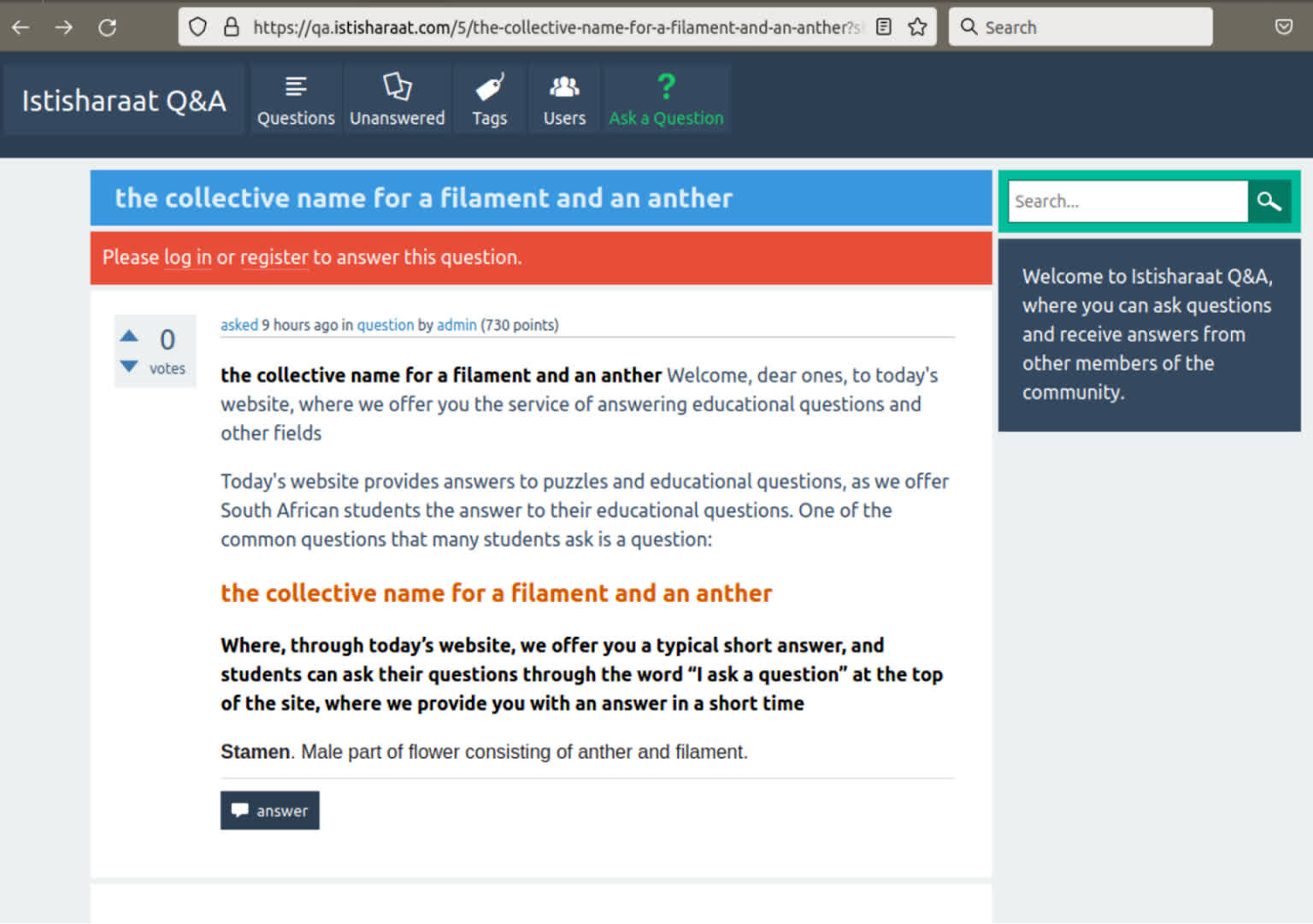
Suspect pages typically have Q&A kinds mentioning Bitcoin or different blockchain-related topics. Savvy customers may assume these websites try to promote Bitcoin or different cryptocurrencies, presumably for a pump-and-dump scheme. That could be the case, however Sucuri theorizes that all the textual content is simply filler content material masking up the rip-off’s precise income stream, Google advert views.
A clue suggesting that is that most of the URLs concerned seem in a browser’s tackle bar as if the person clicked on Google search outcomes resulting in the websites in query. The ruse may very well be an try and disguise the redirects as clicks from search leads to Google’s backend, probably inflating search impressions for advert income. Nevertheless, it’s unclear if this trick works as a result of Google does not register any search consequence clicks matching the disguised redirects.
Sucuri first seen the malware in September, however the marketing campaign intensified after the safety group’s first report in November. In 2023 alone, researchers tracked over 2,600 contaminated websites redirecting guests to over 70 new fraudulent domains.
The scammers initially hid their actual IP addresses utilizing CloudFlare, however the service booted them after the November story. They’ve since migrated to DDoS-Guard, an identical however controversial Russian service.
The marketing campaign primarily targets WordPress websites, suggesting present zero-day WordPress vulnerabilities. Furthermore, the malicious code can cover by means of obfuscation. It may additionally briefly deactivate when directors log in. Website operators ought to safe their admin panels by means of two-factor authentication and guarantee their websites’ software program is up-to-date.
This marketing campaign is not the one current malware drive linked to Google adverts. Malicious actors have additionally been impersonating fashionable software program purposes to unfold malware to customers, gaming Google’s advert rating to seem on the high of search outcomes. For now, these seeking to obtain apps like Discord or Gimp ought to keep away from wanting them up by means of Google.